It's clear that Windows 10 is coming in to the ATMs world but as always Windows Operating system is more designed for desktops than for ATM, so we come up with a list of things that any bank have to take care in any installation of Windows 10, some of the recommendations of this list are generic recommendation that will apply to any Windows 10 O.S. in any hardware vendor and we will live some more personalized recommendation for the end
Observations: This list doesn't include all security recommendations to properly configure windows 10 for ATMs and some of this recommendations have to be review based in the business requirements and ATM networks needs.
- Disable windows key to avoid any special windows function not controlled or coming from some new patch
https://windowsreport.com/disable-windows-key/
- Disable Windows 10 tips
- Disable windows 10 aids using F1 keys

- Disable cortana from windows 10
https://www.howtogeek.com/265027/how-to-disable-cortana-in-windows-10/
- Activation of protection against vulnerabilities in windows 10 and keep all options activated to avoid possible basic exploits of local memory.
- Enable core isolation
- It is important to protect MSXFS.dll from the use or external calls for any malware trying to enter the XFS SPI Services, therefore we strongly recommend that APPlocker is used and protect the use of the MSXFS library from any external not allowed, or not signed by a trusted authority
**This Recommendation does not limit the use of other whitelist software
- We strongly recommend activating applocker and blocking all applications that are not signed by reliable sources, in this way we will add one more layer of security against possible unsigned versions or malware.
- Improve the following GPO policies according to your ATM network needs
Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Defender Antivirus\Windows Defender Exploit Guard\Attack Surface Reduction
- This Observations are only increasing the storage capacity for security event viewer events therefore we recommend taking into account the other event viewer classifications
- On the other hand, it should be noted that in all facilities they are complying with the event storage policies in the event of any unwanted event, their registration must be kept, for that we recommend the following GPOs
- Check that the autoplay and autorun policies are disabled in any of its local disk or external disk modalities.
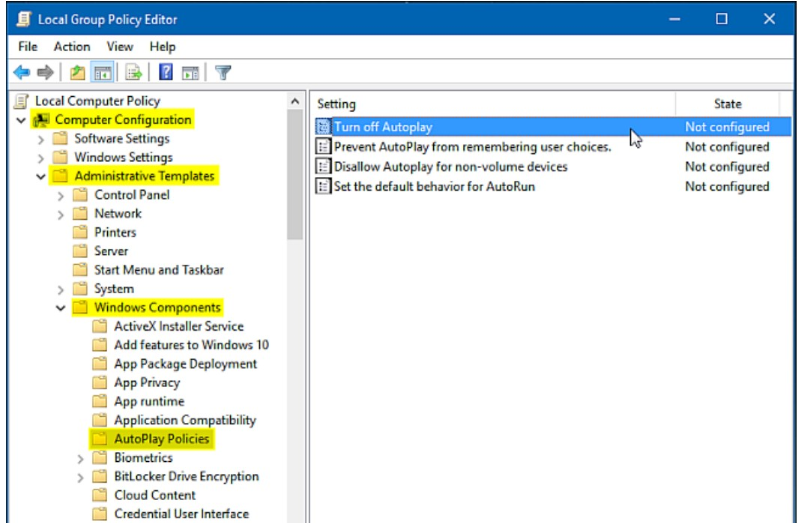
- Review the facilities control policies for when the security software is turned off, eye does not apply to all business models as it can file certain operations to support ATM
- Block access to record modification tools in production
- Review user privilege policies according to business security needs
- Review and keep remote console access prohibited through this disabled GPO:
- Disable TO GO functions of Windows 10
- Always enable view file extensions.
By default Windows File Explorer hides known file extensions. This can be used to deceive the operator, therefore, it is recommended that the user can always view the extensions of all files

- Disable IPv6 if not in use
To decrease attack surfaces and unnecessary network traffic, it is recommended to disable the IP protocol version 6. Microsoft does not recommend disabling support for IPv6 in the operating system, being a better alternative to disable it at the specific network interface level.
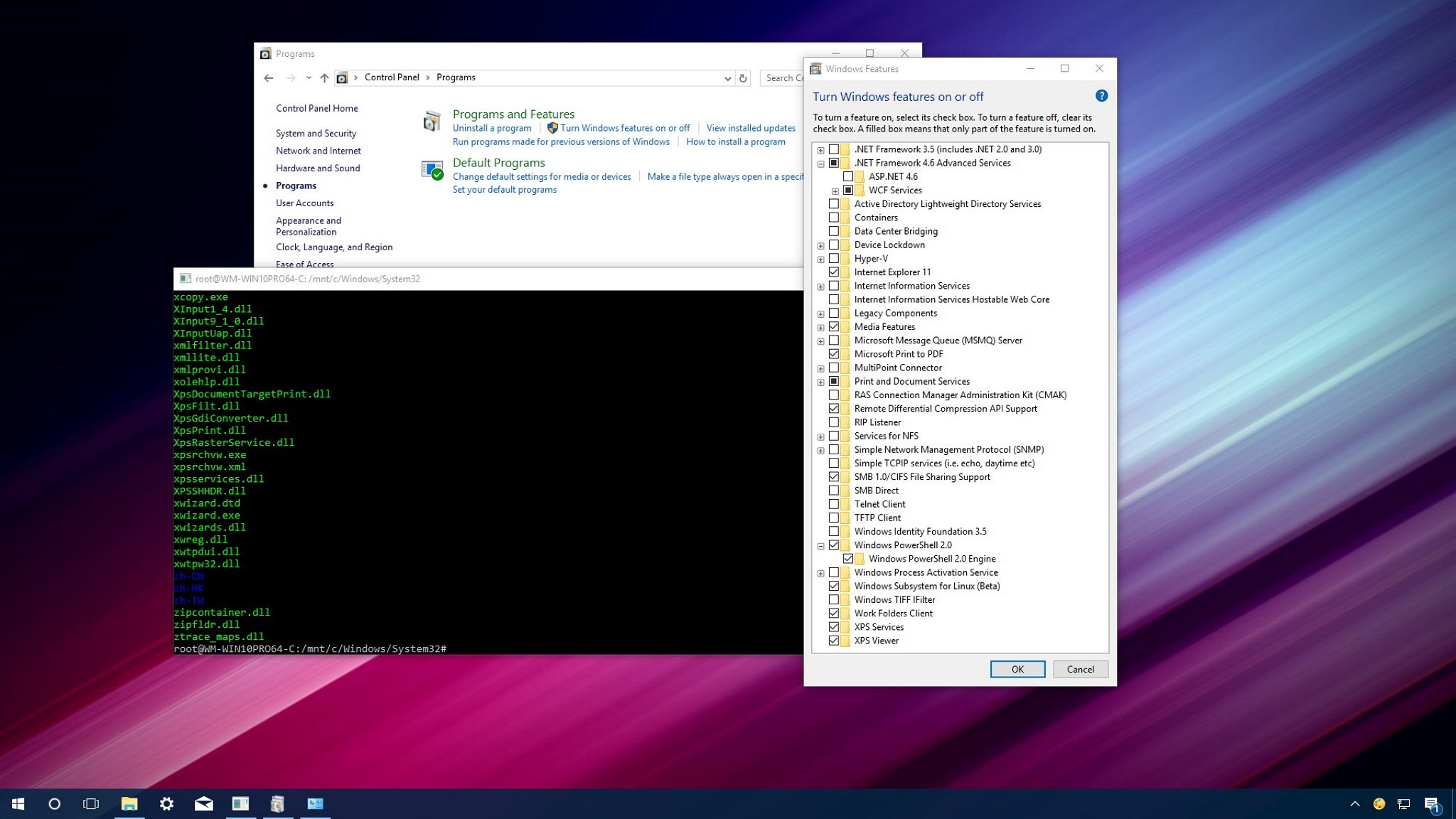
- Disable unnecessary functions
For example for ATMs there is not need of use of powershell , telnet or Windows Subsystem for linux , but please check with your ATM security department
- Block remote desktop access if its not need
https://www.cisecurity.org/white-papers/intel-insights-how-to-disable-remote-desktop-protocol/
- Do not store ATM password using reversible encryption
- Disable automatic maintenance
https://appuals.com/how-to-turn-off-automatic-maintenance-in-windows-10/
- Block automatic defragmentation for the disk
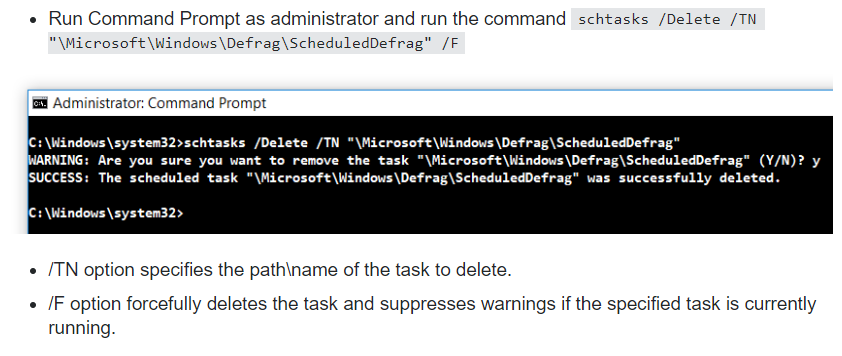
- Delete unnecessary application for ATMs
Disable applications not necessary for the ATM There are some applications that Windows 10 could have pre-installed and that are not necessary for an ATM. In case the Windows 10 edition does have them, you can use Powershell commands to disable them, such as the following:
• Alarms & Clocks: get-appxpackage Microsoft.WindowsAlarms | removeappxpackage
• Calculator: get-appxpackage Microsoft.WindowsCalculator | removeappxpackage
• Camera: get-appxpackage Microsoft.WindowsCamera | removeappxpackage
• Groove Music: get-appxpackage Microsoft.ZuneMusic | removeappxpackage
• Mail & Calendar: get-appxpackage icrosoft.windowscommunicationsapps | remove-appxpackage
• Maps: get-appxpackage Microsoft.WindowsMaps | remove-appxpackage
• Movies & Tv: get-appxpackage Microsoft.ZuneVideo | removeappxpackage
• OneNote: get-appxpackage Microsoft.Office.OneNote | removeappxpackage
• People: get-appxpackage Microsoft.People | remove-appxpackage
• Photos: get-appxpackage Microsoft.Windows.Photos | removeappxpackage
• Voice Recorder: get-appxpackage *Microsoft.WindowsSoundRecorder * | removeappxpackage
• Xbox: get-appxpackage Microsoft.XboxApp | remove-appxpackage
• Mspaint: Get-AppxPackage Microsoft.MSPaint | Remove-AppxPackage
• 3dbuilder: Get-AppxPackage 3dbuilder | Remove-AppxPackage
• Calendar and Mail: Get-AppxPackage windowscommunicationsapps | Remove-AppxPackage
• Camera: Get-AppxPackage windowscamera | Remove-AppxPackage
• Get Office: Get-AppxPackage officehub | Remove-AppxPackage
• Get Skype: Get-AppxPackage skypeapp | Remove-AppxPackage
• Get Started: Get-AppxPackage getstarted | Remove-AppxPackage
•Microsoft Solitaire Collection: Get-AppxPackage solitairecollection | Remove-AppxPackage
• Money: Get-AppxPackage bingfinance | Remove-AppxPackage
• News: Get-AppxPackage bingnews | Remove-AppxPackage
• Phone Companion: Get-AppxPackage windowsphone | Remove-AppxPackage
• Store: Get-AppxPackage windowsstore | Remove-AppxPackage
• Sports: Get-AppxPackage bingsports | Remove-AppxPackage
• Weather: Get-AppxPackage bingweather | Remove-AppxPackage
• Reader: Get-AppxPackage Reader | Remove-AppxPackage• Messaging: Get-AppxPackage Messaging | Remove-AppxPackage
• CommsPhone: Get-AppxPackage CommsPhone | Remove-AppxPackage
• ConnectivityStore: Get-AppxPackage ConnectivityStore | Remove-AppxPackage
• Sway (Office): Get-AppxPackage Office.Sway | Remove-AppxPackage
Please do also consider review this apps
• Microsoft.AAD.BrokerPlugin
• Microsoft.AccountsControl
• Microsoft.BioEnrollment
• Microsoft.LockApp
• Microsoft.Windows.AssignedAccessLockApp
• Microsoft.Windows.CloudExperienceHost
• Microsoft.Windows.ContentDeliveryManager
• Microsoft.Windows.Cortana
• Microsoft.Windows.ParentalControls
- Disable Remote assistance
https://www.prajwal.org/disable-remote-assistance-windows-10/
- There is a replacement for EMET in windows 10 so please review the security policies that can be apply, you can do it through GPO or by GUI, please consider proper security configurations for your devices
- Disable Safe boot in windows 10
https://thetechnologygeek.org/disable-windows-safe-mode/
- Disable SBP-2
The following Device class GUID for an SBP-2 drive:d48179be-ec20-11d1-b6b8-00c04fa372a7
On some platforms, completely disabling the 1394 device may provide extra security. On the previously mentioned website, refer to the "Prevent installation of devices that match these device IDs" section under "Group Policy Settings for Device Installation".
The following is the Plug and Play compatible ID for a 1394 controller:
PCI\CC_0C0010
- And last but not least for the part "I", please consider review the user privileges for accessing the SPI and XFS applications of the XFS vendor, please review with your cyber security department to review all user privilege and reconfigure them



